Wiz security researchers have discovered a vulnerability in the Microsoft Azure Cosmos DB. This can give hackers access to the database environment and the data stored in it. Microsoft has since warned customers about this bug.
Wiz security professionals have discovered that hackers Easy access to the popular Microsoft Azure Cosmos DB. One of the vulnerabilities, dubbed ChaosDB, gave access to all the keys of many end users of the tech giant’s cloud-based database. These end users included major companies such as Citrix, Exxon-Mobil, and Coca-Cola. The keys made it easy to search these clients’ databases, download, manipulate, and delete data.
vulnerability details
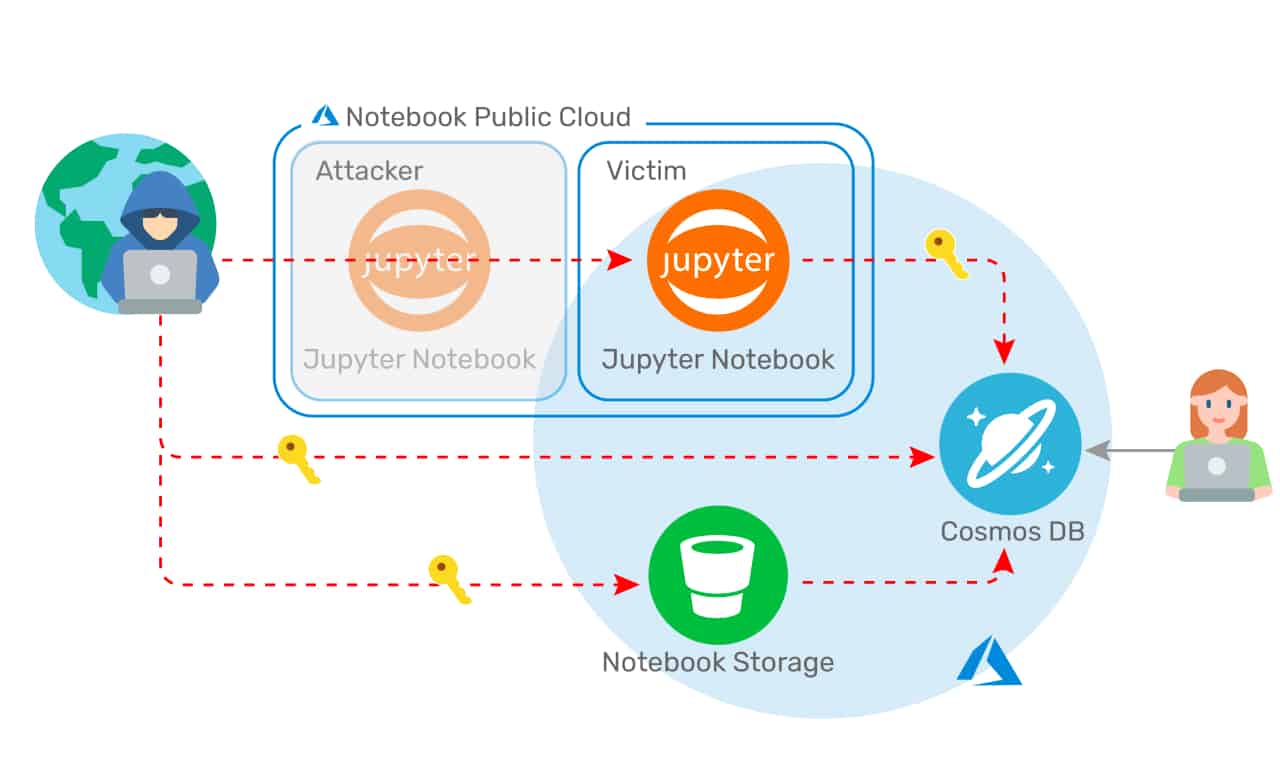
The key access vulnerability is in the Jupyter Notebook functionality that has been included in Cosmos DB as a standard for two years. This allows users to visualize their data in the database and create custom overviews. A number of misconfigurations in the code for this function resulted in a new attack vector.
Wiz does not provide detailed details about this attack vector yet, but in short, according to experts, the notebook container allows privileges to be escalated into other customers’ notebooks. In this way, hackers can gain access to the primary keys of Cosmos DB users and other secrets, such as the access code to the laptop’s large binary data storage.
As a result, hackers can easily access and even take over and alter all the data in the affected database.
Direct action from Microsoft
After Wiz notified Microsoft, the tech giant took action. The notebook functionality is immediately disabled and will remain so until a fix is found. In addition, 30 percent of the most vulnerable customers were advised to use their primary keys to change. Microsoft itself does not have access to these keys.
According to Wiz, the effect is much greater. Experts believe that any Cosmos DB that uses laptop functionality after February of this year is at risk. Also, the vulnerability may be active for months to years. So they ask all end users to change their primary keys.